
Social Media Security Guidance for the C-Suite
Social media channels have substantially boosted executive visibility—and the visibility of their companies. However, the benefits of social media outreach haven’t come without a cost. These highly visible members of the C-suite, and their organizations, have become targets for threat actors through these very social channels.
Social Media Attacks on the C-Suite
Cybercriminals always seek to breach executives’ organizations through various means, but social media gives them additional methods to impersonate executives and harm the organization, including launching phishing attacks to initiate ransomware attacks or steal data and funds. Regardless of threat actors’ motives, experiencing a social media account security incident can cause significant damage to organizations, individuals and brand reputation.
Executive social media attacks specifically focus on the business and personal accounts of C-suite members who lead targeted organizations. By breaching executive social media accounts, threat actors can impersonate executives and use their accounts to post damaging content, wreak havoc on a brand, or use their name and influence to gain inside access to confidential networks, data and finances.
To launch social media attacks, threat actors usually turn to Twitter, LinkedIn and Facebook, which most executives typically use. Execs’ communication with clients and prospects allows easy access to personal, vendor and corporate information.
READ: How to Advance Your Phishing Program to Address Ransomware
Examples of Social Media Breaches
Attackers seek to infiltrate the social media accounts of executives in a variety of ways. They typically will hit vulnerable devices, such as mobile or BYOD, but they also won’t hesitate to go more sophisticated by combining other social engineering ploys and methods to get the access they need.
Recent examples of cybercriminals exploiting executives’ social media accounts include:
- Hijacking accounts of political candidates to direct followers to undesirable websites.
- Sabotaging executives’ accounts to disable them, post illegal content or increase ad spend and rack up thousands of dollars in charges.
- Compromising public organizations’ official accounts and posting derogatory messages.
- Hacking into popular social influencer accounts to post content portraying the influencers in a negative light.
These are only a handful of recent attacks in the U.S., but social accounts everywhere are being continually breached. In many attacks, threat actors routinely impersonate executives and trick others into sharing sensitive financial data, transferring large sums of money or disclosing login credentials.
Social Engineering Attacks on the C-Suite
Attackers use many different types of social engineering attacks, but will often launch phishing attacks after breaching an executive’s social media account.
Targeted phishing attacks directed at C-Suite members are referred to as spear-phishing or “whaling,” and they have become one of the most prominent forms of cyberattacks. The top types of attack include:
- Spear-phishing: This is a phishing attack that targets specific departments or job roles. Attackers research the target and tailor attacks to gain their trust and trick them into providing access or exposing their credentials.
- Business email compromise (BEC): Email accounts of senior executives or financial officers are compromised by exploiting an existing vulnerability, and the accounts are then used to launch a social engineering or spear-phishing attack resulting in financial fraud.
- Whaling: Like spear-phishing, these phishing attacks target specific high-level executives to gain access to critical systems or convince individuals to send large wire transfers.
- Water holing: Attackers either set up spoofed websites or compromise popular sites and then trick victims into visiting the sites and revealing their credentials or other data.
READ: 10 Ways to Identify a Phishing Email
Social Media Attack Prevention for Executives
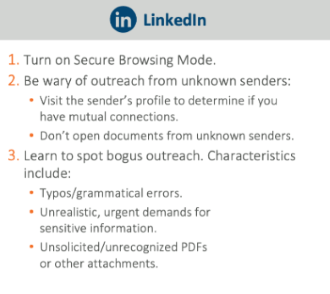
Avoid becoming a victim of a social media attack by learning how to recognize the indicators of a breach. Common signs of malicious attempts to hack social accounts include typos/bad grammar in messages, urgent demands for sensitive information, or unsolicited documents or PDFs.
Follow these best practices to prevent an attack:
- Monitor your accounts for new logins, posts, follows and other suspicious activity.
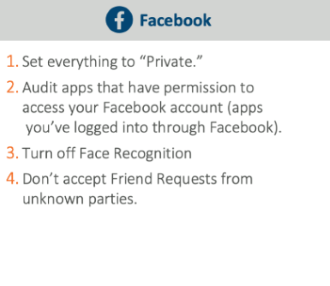
- Review account permissions and restrict access to external apps.
- Don’t accept information requests from unknown entities.
- Limit your contact information in all social media profiles.
- Use complex 16+ character passwords and keep them unique.
- Use two-factor authentication and password reset verification.
- Avoid short message service (SMS)-based two-factor authentication.
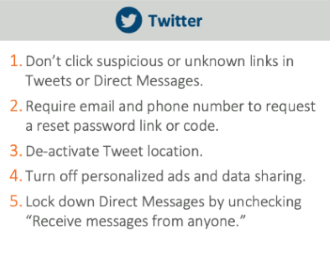
You can also protect yourself by not clicking on suspicious or unknown links, not opening attachments, turning off locators on platforms, restricting incoming private messages, selectively accepting connection requests and carefully vetting unknown senders.
As an executive or C-Suite member, you are automatically a high-profile target. Understanding how to recognize and avoid individual attacks is just the first step. Your security team and employees must be educated in the different types of attacks, and your team should perform continuous training. Lastly, integrating physical protections, such as cybersecurity tools and compliance solutions that offer real-time threat detection and incident response go a long way to preventing large-scale damage.
Tips for Preventing Social Media Attacks Against Executives
- Use a complex, 16+ character password that isn't used for other accounts.
- Turn on two-factor authentication and password reset verification:
- Avoid short message service (SMS)-based two-factor authentication.
- If possible, use an Authenticator app.
- Use a password manager.
- Limit amount of contact information in your profile.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.